This is probably the most often referred to topic both on the forums and here on my blog. After finding it in the top 10 keyword searches to my blog this morning I decided to try and write up a new post that would conclusively answer the question with respect to Avaya (formerly Nortel) Ethernet Routing Switches.
Definitions
Now before I get started lets define some basic terms;
- Access port is defined as a port belonging to a single VLAN
- Trunk port as defined in Wikipedia is a port designed to carry multiple VLANs through a single network link through the use of a “trunking protocol”. To allow for multiple VLANs on one link, frames from individual VLANs must be identified. The most common and preferred method, IEEE 802.1Q adds a tag to the Ethernet frame header, labeling it as belonging to a certain VLAN. Since 802.1Q is an open standard, it is the only option in an environment with multiple-vendor equipment.
So by it’s definition an access port can only belong to one VLAN while a trunk port can belong to multiple VLANs.
It’s important to distinguish that we’re talking about single ports. A trunk group or trunk port group is made up of multiple ports which are combined into a single virtual port. Protocols such as MultiLink Trunking (Avaya), EtherChannel (Cisco) and LACP provide the ability to combine multiple trunk ports into a single virtual interface providing redundancy and additional bandwidth.
Basic Examples
In general the majority of edge switch ports will be configured as access ports. Any port used to connect a personal computer, laptop, server, printer, etc will be configured as an access port. Any port that connects to another switch will be configured as a trunk port.
Complex Examples
With the advent of virtualization VMware servers are often configured and connected to trunk ports. Where as servers would have traditionally been connected to access ports they can also be connected to trunk ports depending on their configurations. The advent of Voice Over IP (VoIP) to the desktop has also had an impact on how edge switches are configured when the desktop or laptop is connected to the IP phone which is in turn connected to the edge switch. I’ll cover that topic in more detail later on.
Avaya Ethernet Routing Switches
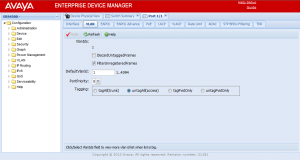 Ethernet Routing Switch 2500, 4000, 5000 Series
Ethernet Routing Switch 2500, 4000, 5000 Series
The Avaya Ethernet Routing Switch 2500, 4000 and 5000 series switches currently offer the following options.
- tagAll – sets the port as a trunk port tagging all frames with an 802.1Q header as they egress the port.
- untagAll – sets the port as an access port stripping all 802.1Q headers as they egress the port.
- tagPvidOnly – sets the port as a trunk port but only adds 802.1Q headers for the PVID VLAN as they egress the port.
- untagPvidOnly – sets the port as a trunk port but only adds 802.1Q headers for every VLAN other than the PVID VLAN as they egress the port.
What is the PVID? The PVID is the Default VLAN ID configured for that specific port. In a typical configuration where the port is an access (untagAll) port the PVID will be set to that VLAN automatically by the switch. In a trunk port configuration the PVID will be used to determine which VLAN to bridge any received untagged frames to if DiscardUntaggedFrames is not enabled. It’s recommended to enable DiscardUntaggedFrames on any port configured as a trunk (tagAll) port to avoid any potential configuration issues which might lead to a loop and a network outage. It’s also a best practice to configure the PVID on all trunk (tagAll) ports with the VLAN ID of your management VLAN.
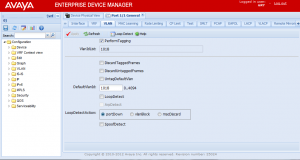 Ethernet Routing Switch 1600, 8600, 8800 Series
Ethernet Routing Switch 1600, 8600, 8800 Series
You’ll notice on the Ethernet Routing Switch 1600, 8600 and 8800 series that the options are slightly different but achieve the same outcome.
- PerformTagging (Checked) – sets the port as a trunk port tagging all frames with an 802.1Q header as they egress the port.
- PerformTagging (Unchecked) – sets the port as an access port stripping all 802.1Q headers as they egress the port.
Additional options include DiscardTaggedFrames, DiscardUntaggedFrames and UntagDefaultVlan. These options can be used to achieve the same results as with the Avaya Ethernet Routing Switch 2500, 4000 and 5000 series switches with the exception of tagPvidOnly.
Is the PVID equivalent to the native vlan command in Cisco switches? It is if untagPvidOnly/UntagDefaultVlan is enabled. The PVID (DefaultVlanId) by itself only acts on untagged received frames. The untagPvidOnly/UntagDefaultVlan option acts on transmitted frames and so the combination of the two equates to the “switchport trunk native vlan #” on a Cisco switch.
It’s also important to point out that Avaya only supports 802.1Q tagging. So while Cisco supports ISL and 802.1Q there is no Avaya command similar to “switchport trunk encapsulation dot1q” since this is the default behavior with Avaya switches.
IP Telephony
There are some special considerations when desktops and laptops are physically connected to the PC port on back of an IP phone and then the IP phone is cabled to the edge switch. In this scenario the common approach is to tag the voice VLAN while leaving the data VLAN untagged. Why? It’s important that we separate the voice traffic from the data traffic so we utilize two different VLANs, one VLAN will carry the voice traffic while one VLAN will carry the data traffic destined to the desktop or laptop. The desktop or laptop probably won’t be configured for 802.1Q tagging so it won’t understand an 802.1Q tagged frame. We need to guarantee that any frames being delivered to the PC port on the back of the IP phone are untagged, if they aren’t the laptop or desktop will just discard the frame. The IP phone will tag the voice frames with an 802.1Q header so the switch will properly bridge those frames to the voice VLAN. In this scenario we need to utilize the untagPvidOnly option in combination with configuring the PVID (DefaultVlanId) as the data VLAN. This way the voice VLAN will be tagged with an 802.1Q header so the phone understands it and the data VLAN will be untagged so the desktop or laptop understands it. The IP phone will be configured with the Voice VLAN ID so it knows which ID to use when communicating with the Call Server and Media Gateways.
Cheers!