 We ran into an interesting problem today with one or our Internet links.
We ran into an interesting problem today with one or our Internet links.
The Internet Service Provider for this (1Gbps) link is AboveNet and the circuit itself is terminated by a Cisco 7301 and then ultimately a pair of Check Point IP560 IPSO v6.2 Security Appliances (firewalls) running Check Point FireWall-1 NGX R70 utilizing VRRP clustering.
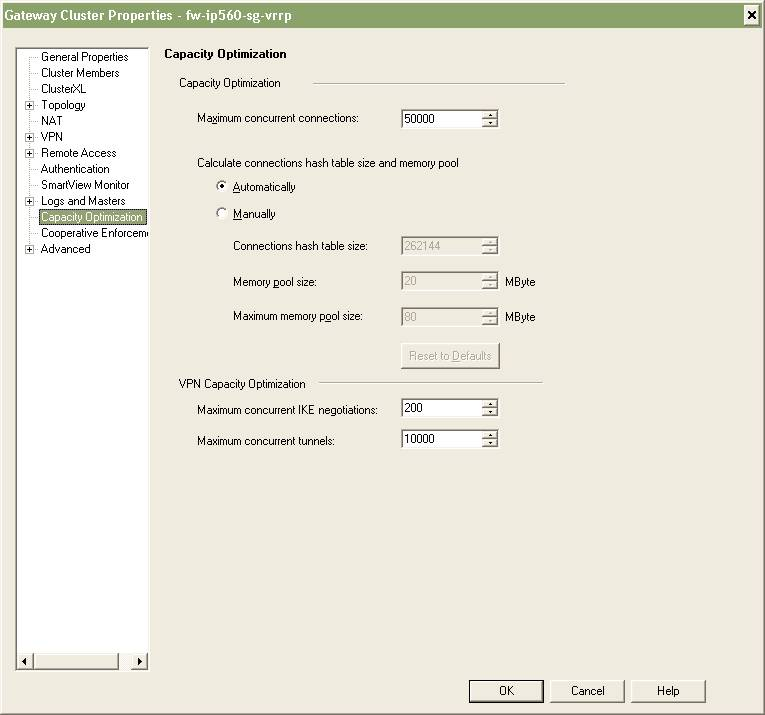
These two IP560s were only installed just recently and only went live two weeks ago so we’re still in the process of working out some of the bugs and refining the security policies. It didn’t take too long to realize that the primary IP560 firewall had 24,900 connections open and that we were hitting the default limit of 25,000 connections.
The obvious fix was to increase the value beyond 25,000. You need to be careful here and take into consideration the amount of memory you physically have available on your security gateway (firewall). I choose 50,000 as a starting point since our IP560s have 2GB of memory installed. I was able to increase the value by editing the Maximum concurrent connections value (Smart Dashboard -> Gateway Cluster Properties -> Capacity Optimization). We also had to push the policy to the cluster before the change took affect.
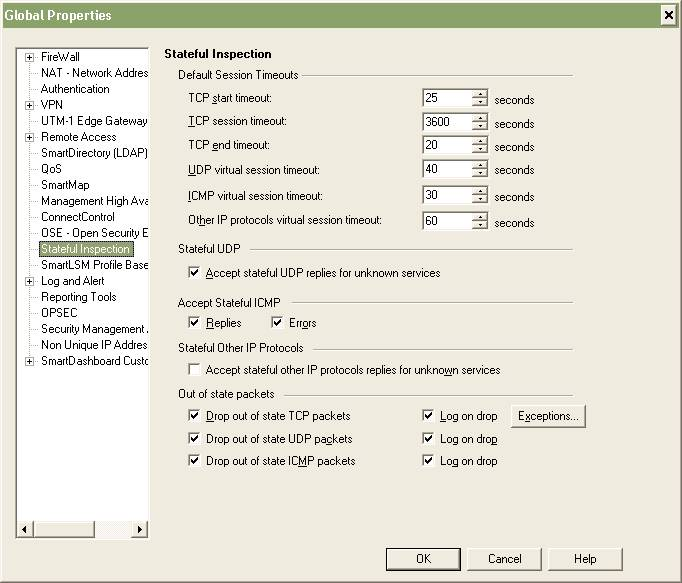
I also took the opportunity to check the TCP timeout value. The TCP timeout is the value that the firewall will use to age out connections in the table if there’s been no activity. This is useful to prevent stale TCP connections from filling your connection table and taking down your firewall. Unfortunately for me I use the same Smart Center environment to manage both my internal and external (Internet) firewalls. This can be a problem since the TCP session timeout value is a global value applied to all firewalls in the Smart Center console. It’s a problem because I have internal firewalls where the TCP session timeout needs to be a fairly large number like 86400 (1 day) and I have external/Internet firewalls where the TCP session timeout needs to be fairly small number like 3600 (1 hour). I haven’t found a workaround to this problem other than making sure I edit the Global Properties policy manually every time I want to push a policy to a specific firewall.
You can find the figure below by selecting Policy -> Global Properties from within Smart Dashboard.
I’m curious what other people use as a value for the maximum number of connections.
The value will obviously be based on the number of devices trying to traverse the firewall, be it internal traffic or Internet traffic. It’s well known that some P2P applications out there can easily create hundreds of connections from a single machine, not to mention all the malware including viruses, trojans, spyware, etc and the number of TCP connections they try to initiate.
Is there anyway for Smart Center to alarm if this value approaches some threshold or limit?
I’m curious what management options there are avialable to have Smart Center alarm or report on the maximum number of connections. I believe the SNMP MIB for Check Point has an OID for the number of active connections but does that mean I need a third party solution to monitor that OID via SNMP like HP OpenView?
Thanks to Steven Drzaszcz for his help via Twitter!
Cheers!