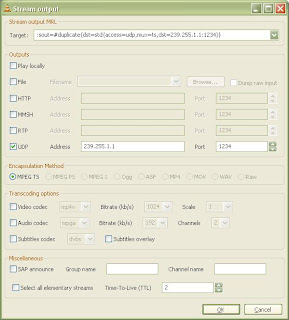
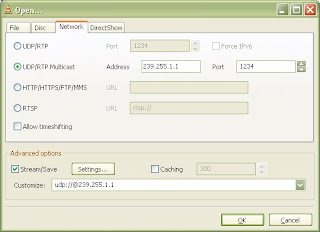
I recently happened upon a familiar problem with IGMP Snooping on a Layer 2 topology comprised of Cisco Catalyst 6504 and 4948 switches. Another team was having issues getting Multicast traffic to pass between their Xen hosts which were all on the same VLAN, but where physically wired to the two different switches mentioned above. There was a trunk interface between the two switches, passing all the VLANs so there was nothing wrong with the basic Layer 2 forwarding. In general Multicast frames will be flooded across all ports in the VLAN, unless IGMP snooping is enabled which it is by default in Cisco switches. I remember quite a few challenges with IGMP snooping back in the Nortel and Avaya days. Avaya eventually changed their default configuration such that IGMP snooping is now disabled by default.
In this specific case all the routing was being performed by a number of high-end Cisco ASA firewalls which didn’t have PIM routing configured or enabled so I took the easy approach of just disabling IGMP snooping across the Cisco Catalyst 6504 and 4948 switches and the problem was solved. The cleaner solution would have been to setup an Mutlicast Router (mrouter) on the VLAN to properly handle all the IGMP requests and reports.
As pointed out by a colleague you can use a great little Python script written by RedHat for testing Multicast on your Linux servers.
Cheers!
Note: This is a series of posts made under the Network Engineer in Retail 30 Days of Peak, this is post number 3 of 30. All the posts can be viewed from the 30in30 tag.
Reference;
http://www.cisco.com/c/en/us/support/docs/switches/catalyst-6500-series-switches/68131-cat-multicast-prob.html
http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/route_multicast.html