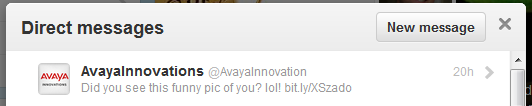
Over the weekend I received a curious direct message on Twitter from @AvayaInnovations with the following text, “Did you see this funny pic of you? lol! bit.ly/XSzado”.
I didn’t attend the recent Avaya Technology Forums in Florida or any other official event recently so the message immediately raised my suspicions such that I left the message alone until this morning. A quick search via the Internet revealed that I wasn’t the only person to receive this curious message. That said I could certainly see more than a few people believing the message to be genuine if they had some interaction with an Avaya employee or partner at the ATF or any other official function or venue which we hear about weekly from this same Twitter account.
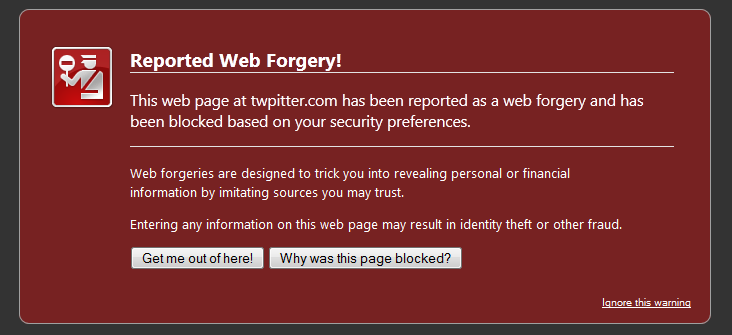 I decided to pursue the actual HTTP link and see where it went. The original link was from Bit.ly which is a link shortening service. These services popped up overnight with the success of Twitter and social networking sites like Facebook to help save space and characters. Unfortunately they have a significant security downfall, in that you don’t really know where the link goes until you actually visit it. See the story by David Weiss entitled, “The Security Implications of URL Shortening Services” for a good explanation. The link from Bit.ly relayed me to twpitter.com which was immediately reported as a web forgery on Mozilla’s Firefox. Mozilla’s Firefox 3 and later incorporates built-in Malware and Phishing protection in participation with Google.
I decided to pursue the actual HTTP link and see where it went. The original link was from Bit.ly which is a link shortening service. These services popped up overnight with the success of Twitter and social networking sites like Facebook to help save space and characters. Unfortunately they have a significant security downfall, in that you don’t really know where the link goes until you actually visit it. See the story by David Weiss entitled, “The Security Implications of URL Shortening Services” for a good explanation. The link from Bit.ly relayed me to twpitter.com which was immediately reported as a web forgery on Mozilla’s Firefox. Mozilla’s Firefox 3 and later incorporates built-in Malware and Phishing protection in participation with Google.
The name of the site was itself very suspicious, twpitter.com. Having a quick look at the WHOIS database told me all that I needed to know.
[Querying whois.verisign-grs.com] [Redirected to grs-whois.hichina.com] [Querying grs-whois.hichina.com] [grs-whois.hichina.com] Domain Name ..................... twpitter.com Name Server ..................... dns9.hichina.com dns10.hichina.com Registrant ID ................... hc292727277-cn Registrant Name ................. yong yi Registrant Organization ......... yi yong Registrant Address .............. Shang Hai City Registrant City ................. Shang Hai Registrant Province/State ....... Shang Hai Registrant Postal Code .......... 200000 Registrant Country Code ......... CN Registrant Email ................ liwei553@hotmail.com Administrative ID ............... hc292727277-cn Administrative Name ............. yong yi Administrative Organization ..... yi yong Administrative Address .......... Shang Hai City Administrative City ............. Shang Hai Administrative Province/State ... Shang Hai Administrative Postal Code ...... 200000 Administrative Country Code ..... CN Administrative Email ............ liwei553@hotmail.com Billing ID ...................... hc292727277-cn Billing Name .................... yong yi Billing Organization ............ yi yong Billing Address ................. Shang Hai City Billing City .................... Shang Hai Billing Province/State .......... Shang Hai Billing Postal Code ............. 200000 Billing Country Code ............ CN Billing Email ................... liwei553@hotmail.com Technical ID .................... hc292727277-cn Technical Name .................. yong yi Technical Organization .......... yi yong Technical Address ............... Shang Hai City Technical City .................. Shang Hai Technical Province/State ........ Shang Hai Technical Postal Code ........... 200000 Technical Country Code .......... CN Technical Email ................. liwei553@hotmail.com Expiration Date ................. 2014-03-09 01:42:03
Looks like the miscreants are up to their old tricks, although you can’t really trust WHOIS either.
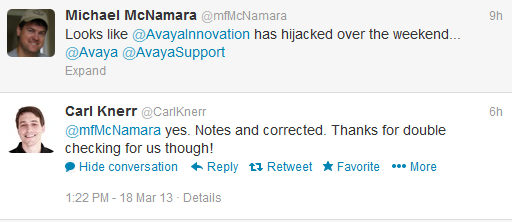
Later in the afternoon I received a follow-up tweet from an Avaya employee;
This is the new attack vector of the miscreants, utilizing trusted sources for spreading their wares. This includes trusted websites along with email and twitter contacts. I was disappointed that I didn’t receive any follow-up from either Avaya or Avaya Innovations. Normally I wouldn’t bother writing a post up about such a trivial matter but I got the impression that Avaya or whoever is managing the Avaya Innovations account was just going to ignore it entirely and pretend that it never happened. Well it did happen and you put our followers at risk! Avaya should at a minimum inform all those users of the issue and provide advice if they happened to visit the link before it was blocked. I took the action of reporting the link to Bit.ly via email.
Cheers!