You’ve patched all your Windows servers and desktop/laptops but what about all the other Windows machines out there that are connected to your network? What about the kioks and Thin Clients and environmental controllers and printer servers, etc? How can you tell if they are patched if you don’t have administrative access to the devices? You can scan your network using a vulnerability scanner. There are many ways to scan your network for machines that are vulnerable to WannaCrypt / WannaCry ransomware but I’ll be talking about using Nmap, a free security scanning tool, in this blog post.
You’ll need the latest version of Nmap v7.40 which you’ll be able to find on Linux (Ubuntu, CentOS, etc) or on Windows thanks to the available binaries for both platforms. I didn’t have any success using Nmap v6.40 which was available via YuM on CentOS 7. So I had to remove Nmap 6.40 (sudo yum erase nmap) and then install the latest RPM version of Nmap which can be found on the downloads page.
I was using CentOS 7 x64 so I issued the following commands;
[mcnamaram1@centos ~]# sudo yum erase nmap [mcnamaram1@centos ~]# wget https://nmap.org/dist/nmap-7.40-1.x86_64.rpm [mcnamaram1@centos ~]# sudo rpm -ivh nmap-7.40-1.x86_64.rpm
Paulino Calderon released a NSE (Nmap Scripting Engine) script on Github that can be easily used with Nmap to detect vulnerable machines. You’ll need to download that script as well.
[mcnamaram1@centos ~]# wget https://raw.githubusercontent.com/cldrn/nmap-nse-scripts/master/scripts/smb-vuln-ms17-010.nse
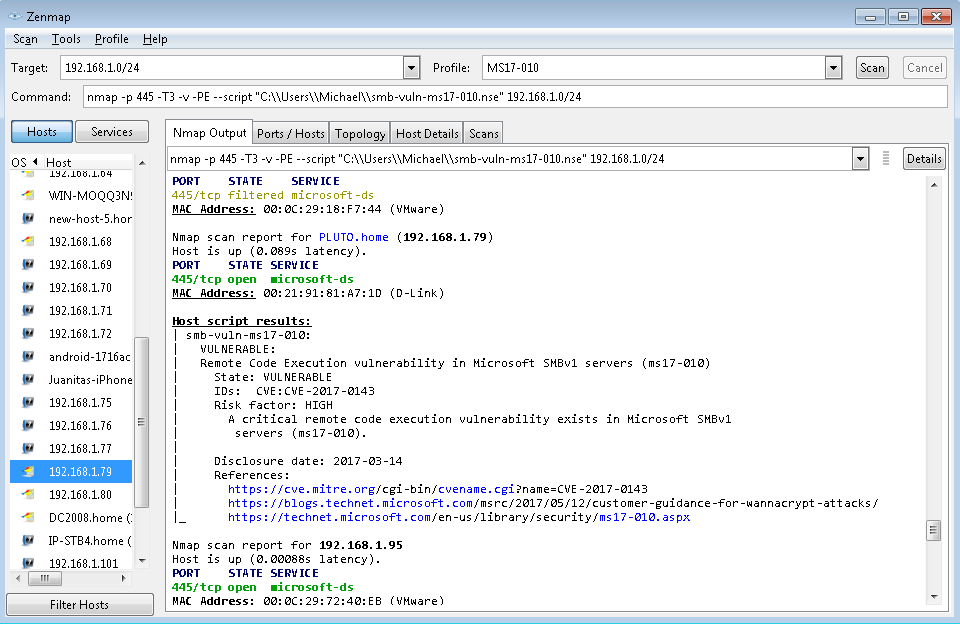
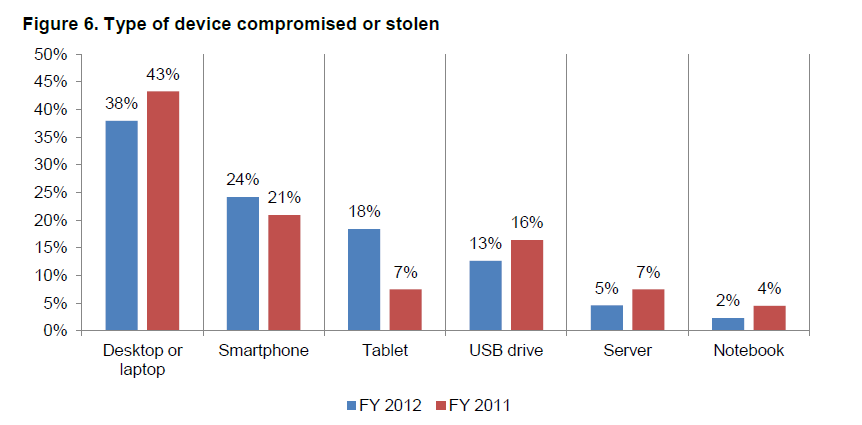
I used the following command line arguments to run the actual scan and found an old Windows XP machine in my home that was vulnerable.
[mcnamaram1@centos ~]# sudo nmap -p445 --script smb-vuln-ms17-010.nse 192.168.1.0/24 Starting Nmap 7.40 ( https://nmap.org ) at 2017-05-15 21:29 EDT Nmap scan report for 192.168.1.0 Nmap scan report for PLUTO.home (192.168.1.79) Host is up (0.058s latency). PORT STATE SERVICE 445/tcp open microsoft-ds MAC Address: 00:21:91:81:A7:1D (D-Link) Host script results: | smb-vuln-ms17-010: | VULNERABLE: | Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010) | State: VULNERABLE | IDs: CVE:CVE-2017-0143 | Risk factor: HIGH | A critical remote code execution vulnerability exists in Microsoft SMBv1 | servers (ms17-010). | | Disclosure date: 2017-03-14 | References: | https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143 |_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
If you’re not a Linux guy or gal you can also use the Windows version of Nmap. The installation was pretty straight forward, I had to download the script to the Windows desktop, create a profile, add the script and select a target. In this case I decided to scan my entire home network IP subnet of 192.168.1.0/24 and the Windows version found the same vulnerable Windows XP desktop;
You’d be surprised what you might find connected to the network.
Good Luck!