We’ve all had SSL certificates expire… however, some are more important than others and have a much broader impact. In February 2020 Microsoft had a certificate expire that brought down Teams as reported by the Engadget in an article titled, Microsoft Teams went down because of an expired certificate. The SSL certificate on the discussion forums that I still maintain was set to expire tomorrow so I thought I should replace it. I could have used Let’s Encrypt for free but I chose to use RapidSSLonline, as it was only $14.99/year for 2 years. I’ve seen too many websites with expired Let’s Encrypt SSL certificates when certbot goes awry or someone forgets to manually renew the certificate every 90 days.
There are hundreds of posts, articles, blogs, video on this topic so I’m going to be extremely brief here. In this case I decided to generate a new private key and essentially a new certificate for forums.networkinfrastructure.info even though I was technically renewing the certificate. I purposely like to keep the FQDNs in the certificate filenames and I keep the files in /etc/ssl/certs for reference in any Apache or Nginx configuration files. For the example below I’ll use my.domain.com to keep the text manageable.
openssl genrsa -out my.domain.com.key 4096 openssl req -new -key my.domain.com.key -out my.domain.com.csr cat my.domain.com.csr
I went online to RapidSSLonline and ordered a SSL certificate, completed the domain validation via email and then cut-n-pasted the contents of the certificate signing request (my.domain.com.csr) into their portal. Waited for the validation and generation and then downloaded the SSL certificate which I stored in a file called my.domain.com.crt. I also downloaded the certificate for the intermediate root, which in this case was for RapidSSL RSA CA 2018. The intermediate root, if any, will change depending on who you use to purchase the SSL certificate.
In order to make sure the certificate chaining was correct, I had to copy the intermediate root certificate along with the certificate I had just downloaded in a single file (bundle).
cat my.domain.com.crt > bundle.my.domain.com.crt cat intermediate.crt >> bundle.my.domain.com.crt
I used the filename bundle-my.domain.com.crt and then copied the private key and the bundle to my server so I could update the Nginx configuration.
ssl_certificate /etc/ssl/certs/bundle-my.domain.com.crt; ssl_certificate_key /etc/ssl/certs/my.domain.com.key; ssl_session_timeout 5m; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers EECDH+AESGCM:EDH+AESGCM:ECDHE-RSA-AES128-GCM-SHA256:AES256+EECDH:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4; ssl_prefer_server_ciphers on; ssl_dhparam /etc/ssl/certs/dhparams.pem;
With that done I checked the Nginx configuration file;
service nginx configtest
And then performed a restart to push the change into production;
service nginx restart
The last step was to visit SSL Shopper to verify the certificate and chaining was all good.
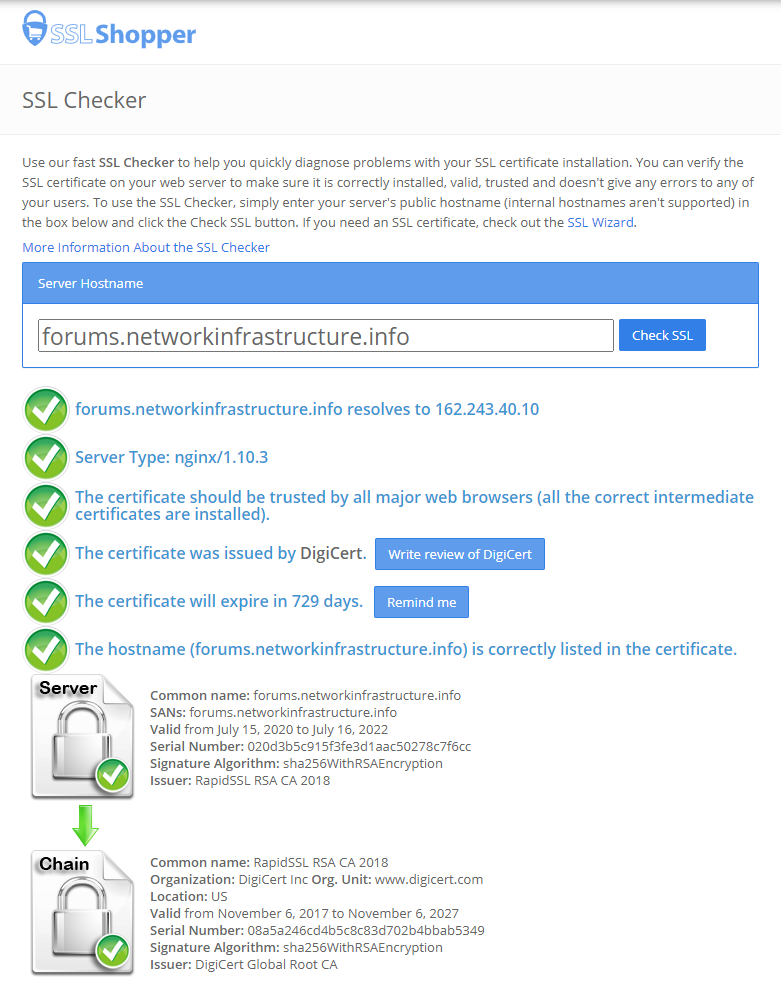
Any questions, let me know.
Cheers!