This is probably the most often referred to topic both on the forums and here on my blog. After finding it in the top 10 keyword searches to my blog this morning I decided to try and write up a new post that would conclusively answer the question with respect to Avaya (formerly Nortel) Ethernet Routing Switches.
Definitions
Now before I get started lets define some basic terms;
- Access port is defined as a port belonging to a single VLAN
- Trunk port as defined in Wikipedia is a port designed to carry multiple VLANs through a single network link through the use of a “trunking protocol”. To allow for multiple VLANs on one link, frames from individual VLANs must be identified. The most common and preferred method, IEEE 802.1Q adds a tag to the Ethernet frame header, labeling it as belonging to a certain VLAN. Since 802.1Q is an open standard, it is the only option in an environment with multiple-vendor equipment.
So by it’s definition an access port can only belong to one VLAN while a trunk port can belong to multiple VLANs.
It’s important to distinguish that we’re talking about single ports. A trunk group or trunk port group is made up of multiple ports which are combined into a single virtual port. Protocols such as MultiLink Trunking (Avaya), EtherChannel (Cisco) and LACP provide the ability to combine multiple trunk ports into a single virtual interface providing redundancy and additional bandwidth.
Basic Examples
In general the majority of edge switch ports will be configured as access ports. Any port used to connect a personal computer, laptop, server, printer, etc will be configured as an access port. Any port that connects to another switch will be configured as a trunk port.
Complex Examples
With the advent of virtualization VMware servers are often configured and connected to trunk ports. Where as servers would have traditionally been connected to access ports they can also be connected to trunk ports depending on their configurations. The advent of Voice Over IP (VoIP) to the desktop has also had an impact on how edge switches are configured when the desktop or laptop is connected to the IP phone which is in turn connected to the edge switch. I’ll cover that topic in more detail later on.
Avaya Ethernet Routing Switches
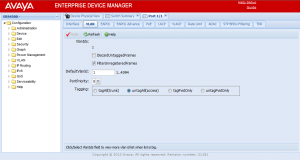 Ethernet Routing Switch 2500, 4000, 5000 Series
Ethernet Routing Switch 2500, 4000, 5000 Series
The Avaya Ethernet Routing Switch 2500, 4000 and 5000 series switches currently offer the following options.
- tagAll – sets the port as a trunk port tagging all frames with an 802.1Q header as they egress the port.
- untagAll – sets the port as an access port stripping all 802.1Q headers as they egress the port.
- tagPvidOnly – sets the port as a trunk port but only adds 802.1Q headers for the PVID VLAN as they egress the port.
- untagPvidOnly – sets the port as a trunk port but only adds 802.1Q headers for every VLAN other than the PVID VLAN as they egress the port.
What is the PVID? The PVID is the Default VLAN ID configured for that specific port. In a typical configuration where the port is an access (untagAll) port the PVID will be set to that VLAN automatically by the switch. In a trunk port configuration the PVID will be used to determine which VLAN to bridge any received untagged frames to if DiscardUntaggedFrames is not enabled. It’s recommended to enable DiscardUntaggedFrames on any port configured as a trunk (tagAll) port to avoid any potential configuration issues which might lead to a loop and a network outage. It’s also a best practice to configure the PVID on all trunk (tagAll) ports with the VLAN ID of your management VLAN.
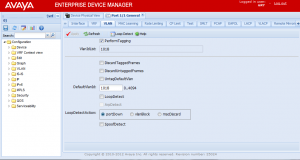 Ethernet Routing Switch 1600, 8600, 8800 Series
Ethernet Routing Switch 1600, 8600, 8800 Series
You’ll notice on the Ethernet Routing Switch 1600, 8600 and 8800 series that the options are slightly different but achieve the same outcome.
- PerformTagging (Checked) – sets the port as a trunk port tagging all frames with an 802.1Q header as they egress the port.
- PerformTagging (Unchecked) – sets the port as an access port stripping all 802.1Q headers as they egress the port.
Additional options include DiscardTaggedFrames, DiscardUntaggedFrames and UntagDefaultVlan. These options can be used to achieve the same results as with the Avaya Ethernet Routing Switch 2500, 4000 and 5000 series switches with the exception of tagPvidOnly.
Is the PVID equivalent to the native vlan command in Cisco switches? It is if untagPvidOnly/UntagDefaultVlan is enabled. The PVID (DefaultVlanId) by itself only acts on untagged received frames. The untagPvidOnly/UntagDefaultVlan option acts on transmitted frames and so the combination of the two equates to the “switchport trunk native vlan #” on a Cisco switch.
It’s also important to point out that Avaya only supports 802.1Q tagging. So while Cisco supports ISL and 802.1Q there is no Avaya command similar to “switchport trunk encapsulation dot1q” since this is the default behavior with Avaya switches.
IP Telephony
There are some special considerations when desktops and laptops are physically connected to the PC port on back of an IP phone and then the IP phone is cabled to the edge switch. In this scenario the common approach is to tag the voice VLAN while leaving the data VLAN untagged. Why? It’s important that we separate the voice traffic from the data traffic so we utilize two different VLANs, one VLAN will carry the voice traffic while one VLAN will carry the data traffic destined to the desktop or laptop. The desktop or laptop probably won’t be configured for 802.1Q tagging so it won’t understand an 802.1Q tagged frame. We need to guarantee that any frames being delivered to the PC port on the back of the IP phone are untagged, if they aren’t the laptop or desktop will just discard the frame. The IP phone will tag the voice frames with an 802.1Q header so the switch will properly bridge those frames to the voice VLAN. In this scenario we need to utilize the untagPvidOnly option in combination with configuring the PVID (DefaultVlanId) as the data VLAN. This way the voice VLAN will be tagged with an 802.1Q header so the phone understands it and the data VLAN will be untagged so the desktop or laptop understands it. The IP phone will be configured with the Voice VLAN ID so it knows which ID to use when communicating with the Call Server and Media Gateways.
Cheers!
Hi Mike, i have a Baystack 470 24G that im trying to trunk with the GBIC modules to a Cisco 3550 and having a heck of a time. i have tried numerous things but i just cant seem to get the cisco GBIC to talk to the Baystack. The Baystack link light turns on, and the CLI says the link is up, but the Cisco 3550 just doesnt like it. Any ideas on how i can get these two working together? thanks man, i really appreciate your help.
-mike
Hi Mike,
The BayStack 470-24T doesn’t support auto-negotiation on the GBIC ports so you need to set the Cisco 3550 for 1000Mbps/Full Duplex.
You can use the following command on the Cisco 3550 to check what the interface supports;
show interface capabilities
The assuming it’s Gigabit capable you can issue the following commands on the Cisco switch;
interface
speed 1000
duplex full
exit
I have noticed some issues between the really old CatOS switches and the Avaya/Nortel switches but this would be my first step.
Good Luck!
Thank you sir, i really appreciate the fast response. Your suggestion just matched another i just read so im am hoping this fix action will do the trick. I have been fighting this for a couple of days and refused to believe that it wasnt possible. I did download the newest software release (12.2.44-se6) for the 3550. The version i downloaded is the un-encrypted version. Would that work better with the Baystack, or would the encrypted 3550 software be better? thanks again boss!!
It’s really an issue with the GBIC and chipsets than a software issue. In the PoE versions of the Ethernet Switch (formerly BayStack) 470 the chipset supports auto-negotiation on the GBIC/SFP ports. In the versions before that though there is no support for auto-negotiation on the GBIC/SFP ports.
I wouldn’t touch the software until you’ve had an opportunity to test the recommended fix.
Good Luck!
Good deal, thanks again Mike. I will let you know how it goes. Have a great night!!
I was just thinking in regards to the baystack programming. When i was logged in to the Baystack, i didnt understand at the time why the GBIC speeds were locked at 1000MB and there was no ability to change the autonogotiation speeds, now it makes sense the only alternative is to change the speed on the 3550. So if you dont mind one last question… why doesnt the Cisco autonogotiate on their GBIC to talk to the baystack?
heres my config, with your suggestion. can you confirm this correct for me?
interface GigabitEthernet0/1
switchport trunk encap dot1q
speed 1000
duplex full
switchport mode trunk
no switchport mode access
no shutdown
Hi Mike,
Autonegotiation requires 2-way communications. In this case the Cisco box is shouting out “I can do…” and the Nortel box is keeping silent. The 3550 should be able to determine what speed the link is running at, but not the duplex and by default will set it to half-duplex (don’t believe there is a way of changing this) which is the opposite of the BayStack.
Essentially, when configuring uplinks between different kit, always check the autonegotiation settings, see wikipedia for more info.
ok mike heres the latest, i got the cisco to link with the baystack, but unfortunately i cant ping from the cisco to any of my baystacks. thoughts?
Hi Mike,
You’ve gotten Layer 1 to work, now you need to verify that your Layer 2 and Layer 3 configurations are correct.
You can read this post for an example of how to setup 801.1Q tagging between an Avaya and Cisco switch.
http://blog.michaelfmcnamara.com/2011/01/802-1q-vlan-tagging-on-a-cisco-catalyst-3750-e/
Good Luck!
Hi Michael,
I am connecting a WatchGuard Firebox device to our ERS 4526 on port 24 and I assume that the port should be a trunk port? Would it be possible for you to quickly review my ERS 4526 configuration for this connection and let me know if I am missing anything. The firebox has an IP address of 192.168.12.81:
enable
configure terminal
vlan configcontrol flexible
vlan port 24 tagging TagAll
vlan create 300 name “Name” type port
vlan members add 300 24
interface vlan 300
ip address 192.168.12.83 255.255.255.240 4
exit
ip routing
ip route 172.16.2.32 255.255.255.240 192.168.12.81 1
ip route 192.168.12.80 255.255.255.240 192.168.12.81 1
ip route 200.32.104.227 255.255.255.255 192.168.12.81 1
ip route 200.32.104.228 255.255.255.255 192.168.12.81 1
Hi Khalil,
You’ve configured the WatchGuard Firebox with the same VLAN ID and appropriate IP addressing?
Good Luck!
Hi Michael,
Can not be any better explanation but “It’s also a best practice to configure the PVID on all trunk (tagAll) ports with the VLAN ID of your management VLAN.” it’s no really secure, right ?
wp4suso
Hi wp4suso,
You can use whatever VLAN ID you’d like, the point is that they should match. I have seen issues with SONMP when the PVID is set to different VLANs between two switches. In my network it’s the same for every closet and it’s a known value everywhere (VLAN 200). Since it’s a fixed constant it’s much easier to configure and work with. If it was different at every site then I would need to look it up somewhere and it could be different at every site.
Cheers!
Thanks for your post, it was the first I have found to explain VLAN tagging on Avaya equipment. I have an Avaya 5632 ERS, and two HP 3com switches downstream. The HP switches extend VLANs to another building. One of them has complete connectivity to the VLANs. Another cannot get anywhere. The HP configurations are identical except for the IP info. I feel the issue is how the connected port on the Avaya is set.
Here is the VLAN information
vlan ports 1/1-24,2/20,2/22,2/46-47 tagging tagAll
vlan ports 2/48 tagging unTagPvidOnly
vlan configcontrol flexible
vlan members 1 1/1-32,2/11-43,2/45-50
vlan members 6 1/1-24
vlan members 150 1/1-24,2/1-10,2/20,2/22,2/48
vlan ports 1/3,1/12 pvid 6
vlan ports 2/1-10 pvid 150
no auto-pvid
The port on the Avaya connected to the working switch is 1/12. The non-working HP switch is connected to 1/8. This switch will mainly be VLAN 1 devices that need to communicate with all three VLANSDo you see what might be causing the issue? Thanks.
Hi David,
If post to the discussion forums you’ll get a much quicker response.
http://networkinfrastructure.info
Cheers!
Hi Michael,
I’m in the process of swapping out some Nortel 4548 switches with Cisco Nexus devices and I’m trying to decipher the Nortel configs but I’m seeing what looks to be a conflict.
Below is a snapshot of the config. Ports 5-34 are untagged so my take is they are access ports but the vlan membership cmds allow multiple vlans on some of those ports. How can the config allow multiple vlans on an access port? For example; port 12 has vlan 172 as its PVID but it is also a member of vlans 170 and 163. Is this a mis-configuration?
—————————————————–
vlan ports 5-34 tagging unTagAll filter-untagged-frame disable filter-unregist ered-frames enable priority 0
vlan members 1 NONE
vlan members 163 1-11,13-14,36,42,46-48
vlan members 170 1-2,5-48
vlan members 172 3-4,12,15,36-37,39,42-43,46-48
vlan ports 3-11 pvid 163
vlan ports 12 pvid 172
vlan ports 13-14 pvid 163
vlan ports 15 pvid 172
vlan ports 16-34 pvid 5
Hi Bill,
It’s a grey area. If you have autopvid set to strict the switch will error on that configuration. Not knowing anything else about your environment I would assume they are access ports.
Cheers!
Michael,
Thanks for the quick reply!
The config includes “no auto-pvid”.
So with the following config on another 4548, port 12 is untagged but its a member of
vlan 6,160,161,162,163,170,172,173 & 180:
vlan ports 12-16 tagging unTagAll filter-untagged-frame disable filter-unregis
tered-frames enable priority 0
vlan members 1 NONE
vlan members 6 3,9,11-13,20,31,37,41-48
vlan members 160 1,4,10-13,19,32,38,41-48
vlan members 161 2,4,10-13,15,19,32,38,41-48
vlan members 162 4,9-13,19,32,38,41-48
vlan members 163 3-5,7-8,10-13,16-17,19-20,22,27-28,32,38,41-48
vlan members 170 1-5,7-13,15-23,27-48
vlan members 172 1,4,6,8,10-14,17-21,23-26,29,32,34-35,38-39,41-48
vlan members 173 2,5,11-13,18,23,25,30,33,36,40,43-48
vlan members 180 1-5,7-13,15-48
vlan ports 11-13 pvid 173
When traffic ingresses on port 12 untagged, which vlan is it sent over? When broadcast or unknown DA traffic comes into the switch, on other ports on these vlans, is it sent out port 12?
Am I right in assuming in the Nortel world untagged (access) ports should be a member of a single pvid vlan with “no auto-pvid” configured?
Thanks,
Bill
did you get your reply? i have same question too.
Hi Michael
I want to connect 2 avaya layer 3 switches using trunk.
a)Ist switch has vlan 5 for voice and val 10 for data
b)2nd switch has vlan 5 for voice and vlan 20 for data
I need to make communication between vlan 10 and vlan 20.Can you plz post the config?
I am trying to connect an Avaya 4524GT-PWR switch to an Cisco SG-300 switch via the SFP ports, and I can not communicate between switches… both switches are factory defaults except for their IP addresses which are both on the 192.168.2.x subnet. Currently we have a Cisco SG-300 in place communicating the the other Cisco SG-300 switch via the SFP port and it works great, if I replace one of the Cisco Switches with the Avaya switch, we can not communicate… any ideas on how to get this working?
Hi Michael,
First of all thanks for all the blogs you wrote on Avaya, saved me in lot of situations.
I got a question, in regards to traffic on VLAN1 between Nortel 5520 to Arista switch. The connections between them is a trunk connection.
For eg: i tagged 1,3,4,5….50 between them.
In Nortel port configs, i have got 2 things a) “DiscardUntaggFrames” checkbox is “ticked” b) DefaultVlanid:4 and got an IP on VLAN1 – 10.10.10.1/24
On Arista side, i have trunked the same vlans & configured an SVI for VLAN 1 – 10.10.10.2/24
But i couldn’t ping each other. Unless I “un-check” the “DiscardUntaggFrames” & change “DefaultVlanId:1”, then it pings.
Did some packet capture on Arista and Avaya side when defaultvlanid:4 . When a packet leaves Arista it’s tagged on VLANID:1 but when it’s hitting Avaya they are putting them into VLANID:4 , why is that? i thought VLAN 1 is tagged ??
Can you please advise ? It’s affecting our production traffic at this stage.
Thanks
Hari
Hi Hari,
The Arista is not tagged the frames in VLAN 1, hence they are untagged, hence they are being discarded.
This is similar to Cisco’s native VLAN command, frames in those VLANs are not tagged across a trunk interface.
Cheers!
Hi Micheal
I have being working on our new VoIP Vlan and tried to configured the switch port with untagPVIDonly with Data VLAN as PVID vlan and it did not work, then when I changed the tagPvidonly with Data VLan as PVID VLan it worked with this setup it means that data Vlan is being tag and Voice VLAN dont, so according to your article it should not work as laptop and desktop will discard andy packet which has been tag by 801.2Q tagging as they dont understand the packet.
Please explain.
Thanks
Hi Mike, i have a ERS 4850 GTS PWR+ that im trying to trunk with the GBIC modules to a vsp 9000 and i have tried many things but i just cant seem to get the vsp GBIC to talk to the ERS 4850. The ERS switch 4850 uplink light turns on, and the CLI says the link is up, but on other side vsp 9000 it’s showing link is down Any ideas on how i can get these two working together?
I would suggest you confirm that you are using the same SFP or GBIC on each side…replace the fiber patch, replace the optic.
Good Luck