It was recently pointed out to me that I had never written a post documenting how to configure SMLT to a edge/closet switch. While there are plenty of examples in the Avaya/Nortel technical guides I’ll humor the folks that are interested. In this example I’ll configure a pair of ERS 8600 switches utilizing SMLT over SLT (Single Link Trunks).
Let’s assume that these switches are already setup in an IST pair (future post?) and that we want to add a new edge/closet switch to the network. We’ll utilize port 1/7 on both ERS 8600 switches to connect to ports 1/47 and 1/48 on the edge switch. The edge switch should be setup as an MLT. You can refer to this post for additional details regarding how to configure the edge switch.
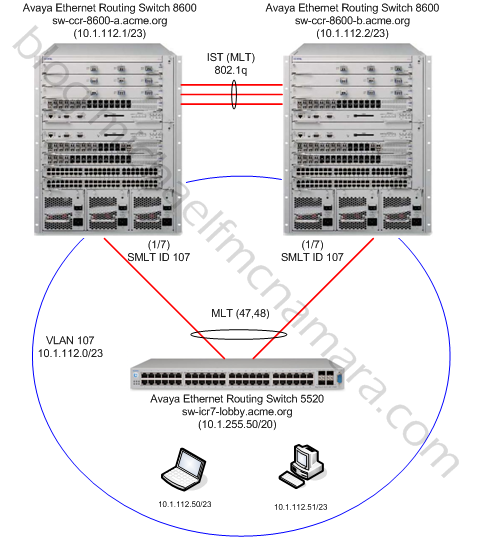
Here’s a diagram of our example topology…
Step 1.
Let’s start configuring the ERS8600-A switch;
config ethernet 1/7 perform-tagging enable config ethernet 1/7 untagged-frames-discard enable config ethernet 1/7 default-vlan-id 200 config ethernet 1/7 cp-limit enable multicast-limit 7500 broadcast-limit 5000 config ethernet 1/7 enable-diffserv true config ethernet 1/7 slpp packet-rx enable config ethernet 1/7 slpp packet-rx-threshold 5 config ethernet 1/7 mstp cist forceportstate disable config ethernet 1/7 mstp msti 1 forceportstate disable config ethernet 1/7 smlt 107 create config ethernet 1/7 vlacp enable config ethernet 1/7 vlacp fast-periodic-time 500 config ethernet 1/7 vlacp timeout short config ethernet 1/7 vlacp timeout-scale 5
Let’s break down those commands and review each;
- config ethernet 1/7 perform-tagging enable
This command will enable tagging to make the port an 802.1q trunk port. This will enable us to trunk multiple VLANs over the single interface, it will also preserve an Layer 2 QoS/CoS information.
- config ethernet 1/7 untagged-frames-discard enable
This command will discard any non 802.1q tagged frames that are received on the port. This can be a valuable defense measure in protecting your network. What would happen if the edge switch was accidentally factory reset with both uplinks still connected? A loop would result, however, with this feature all frames from the edge switch will be discarded until the switch is reconfigured.
- config ethernet 1/7 default-vlan-id 200
This command will set the PVID to our management VLAN. This value will only be considered if the port receives a frame which doesn’t have an 802.1q header and hence is missing the VLAN ID. The command “untagged-frames-discard enable” essentially negates this command but we set it anyway so we’re consistent in our configurations.
- config ethernet 1/7 cp-limit enable multicast-limit 7500 broadcast-limit 5000
This command will enable CP-Limit to protect the core network from too many Multicast or broadcast packets flooding the link. CP-Limit will shutdown the link to try and protect the core network. This is just one of many defense mechanisms available to help protect your network.
- config ethernet 1/7 enable-diffserv true
This command will enable DiffServ (Layer 3 QoS) on the switch port and set it for Trusted, so the switch will honor all DiffServ marked packets and give those packets the appropriate priority and queuing.
- config ethernet 1/7 slpp packet-rx enable
- config ethernet 1/7 slpp packet-rx-threshold 5
These commands will enable Simple Loop Protection Protocol (SLPP) to help detect any misconfiguration of the MultiLink trunks on the edge/closet switch.
- config ethernet 1/7 mstp cist forceportstate disable
- config ethernet 1/7 mstp msti 1 forceportstate disable
These commands will disable Multiple Spanning Tree Protocol (MSTP) no the switch ports. Spanning Tree is not compatible with Avaya’s Split Trunking Protocol since we are quite literally creating a loop in the physical topology. If this switch was running STP the command would like so, ethernet 1/7 stg 1 stp disable.
- config ethernet 1/7 smlt 107 create
Here’s the command that you’ve been waiting for … this command essentially creates a S-SMLT or Single Link Trunk (SLT). The ID used in the connection needs to match the peer ERS 8600 switch.
Design note – in my networks I use numbers to denote the different IDFs or ICRs. I usually add 100 to those numbers for the SMLT ID and VLAN IDs. Since this is IDF #7 (or ICR #7) the SMLT ID is 100 + 7 = 107 and the VLAN for this closet will eventually be 107. If I was still using VRRP the VRRP ID would also be 107. You can use whatever number you’d like but they must match on the two ERS 8600s!
- config ethernet 1/7 vlacp enable
- config ethernet 1/7 vlacp fast-periodic-time 500
- config ethernet 1/7 vlacp timeout short
- config ethernet 1/7 vlacp timeout-scale 5
These commands enable VLACP on the port and utilize the recommended values from Avaya.
You should repeat the commands above in Step 1 on both Avaya Ethernet Routing Switch 8600s, substitute the appropriate port numbers and SMLT ID.
Design note – in my networks the edge/closet switches are still Layer 2 only so I perform all the routing in the core switches. I will usually have a “default” VLAN per edge/closet switch although I do have multiple VLANs that span multiple edge/closet switches.
Step 2.
With the port configured now we’ll build the VLAN that we’ll associate with most ports on the edge switch.
config vlan 107 create byport-mstprstp 1 name "10-1-112-0/23" config vlan 107 add-mlt 1 config vlan 107 ports add 1/7 member portmember config vlan 107 fdb-entry aging-time 21601 config vlan 107 ip create 10.1.112.1.1/255.255.254.0 mac_offset 0 config vlan 107 ip igmp proxy-snoop enable config vlan 107 ip igmp snoop enable config vlan 107 ip dhcp-relay enable config vlan 107 ip ospf interface-type passive config vlan 107 ip ospf enable config vlan 107 ip rsmlt enable config vlan 107 ip rsmlt holdup-timer 9999
Let’s break down those commands and review each;
- config vlan 107 create byport-mstprstp 1 name “10-1-112-0/23”
This command will create VLAN 107 and make it a port based VLAN with the name “10-1-112-0/23”. You might be asking what the mstprstp is… this specific switch I’m working with has been deployed with MSTP enabled. If you have a switch still using STP (default) then the command would look like so config vlan 107 create byport 1 name “10-1-112-0/23”
- config vlan 107 add-mlt 1
This command will add VLAN 107 to our IST which in this case happens to be MLT ID 1.
- config vlan 107 ports add 1/7 member portmember
This command will add VLAN 107 to port 1/7 which we are using to connect our edge/closet switch.
- config vlan 107 fdb-entry aging-time 21601
This command will set the default FDB aging time for all MAC information learned in this VLAN to 6 hours and 1 second. This is a best practice recommendation by Avaya to help reduce the ARP broadcast storms that can result when the FDB table expires a large number of entries which then in turn causes them to be removed from the ARP table causing the switch to re-ARP for them.
- config vlan 107 ip create 10.1.112.1.1/255.255.254.0 mac_offset 0
This command will configure a Layer 3 interface on VLAN 107 with the IP address of 10.1.112.1/23. Your mac_offset will differ depending on how many IP interfaces you already have deployed on your switch.
- config vlan 107 ip igmp proxy-snoop enable
- config vlan 107 ip igmp snoop enable
This command will enable IGMP snooping and proxy on the VLAN.
- config vlan 107 ip dhcp-relay enable
- config vlan 107 ip dhcp-relay create-fwd-path server 10.1.1.100
- config vlan 107 ip dhcp-relay enable-fwd-path server 10.1.1.100
These commands will enable DHCP relay on the VLAN, and forward all DHCP requests to 10.1.1.100.
- config vlan 107 ip ospf interface-type passive
- config vlan 107 ip ospf enable
This command will enable OSPF on the VLAN and will set it to passive (best practice for edge/closet VLANs).
- config vlan 107 ip rsmlt enable
- config vlan 107 ip rsmlt holdup-timer 9999
This command will enable RSMLT which replaces the VRRP functionality. We set the holdup-timer to infinity, we don’t want the ERS 8600 to stop accepting packets for it’s peer at anytime.
You should repeat the commands above in Step 2 on both Avaya Ethernet Routing Switch 8600s, substitute the appropriate IP address and ports.
Step 3.
There are a few items that we still need to take care of to round out the configuration.
We need to enable SLPP for VLAN 107;
- config slpp operation enable
- config slpp add 107
These commands will enable SLPP globally and will also enable SLPP in VLAN 107.
Step 4.
Here are some commands you can use to verify the configuration and operation.
You can check the SMLT table and verify that the trunk is configured as SMLT and operating as SMLT;
ERS-8610-A:5# show smlt info ================================================================================ Mlt SMLT Info ================================================================================ MLT SMLT ADMIN CURRENT ID ID TYPE TYPE -------------------------------------------------------------------------------- 4 4 smlt smlt 10 10 smlt norm 15 15 smlt norm ================================================================================ Port SMLT Info ================================================================================ PORT SMLT ADMIN CURRENT NUM ID TYPE TYPE -------------------------------------------------------------------------------- 1/7 3 smlt smlt 4/4 6 smlt smlt
You can check the MLT table and verify that VLAN 107 is a member of MLT 1 (IST);
ERS-8610-A:5# show mlt info ================================================================================ Mlt Info ================================================================================ PORT SVLAN MLT MLT PORT VLAN MLTID IFINDEX NAME TYPE TYPE ADMIN CURRENT MEMBERS IDS -------------------------------------------------------------------------------- 1 6144 MLT-IST trunk normal ist ist 1/1,4/1,8/1 1 2 3 4 5 9 10 20 21 25 99 100 101 102 103 107 198 199 200
You can verify that the IST is up and operational between the two ERS 8600 switches;
ERS-8610-A:5# show mlt ist info ================================================================================ Mlt IST Info ================================================================================ MLT IP VLAN ENABLE IST ID ADDRESS ID IST STATUS -------------------------------------------------------------------------------- 1 10.1.100.2 100 true up
You can check the state of VLACP on port 1/7 to confirm that VLACP is enable and up.
ERS-86010-A:5# show port info vlacp port 1/7 ================================================================================ VLACP Information ================================================================================ INDEX ADMIN OPER PORT FAST SLOW TIMEOUT TIMEOUT ETHER MAC ENABLED ENABLED STATE TIME TIME TIME SCALE TYPE ADDR -------------------------------------------------------------------------------- 1/7 true true UP 500 30000 short 5 0x8103 01:80:c2:00:11:00
You can check the SONMP topology tables to make sure you have the correct port(s).
ERS-8610-A:5# show sys topology ================================================================================ Topology Table ================================================================================ Local Rem Port IpAddress SegmentId MacAddress ChassisType BT LS CS Port -------------------------------------------------------------------------------- 0/0 10.1.1.1 0x000000 0004387xxxxx ERS8610 12 Yes HtBt 0/0 1/1 10.1.1.2 0x000101 000fcdfxxxxx ERS8610 12 Yes HtBt 1/1 1/7 10.1.255.20 0x00012f 0014c73xxxxx mBayStack5520-48T-PWR 12 Yes HtBt 1/47
Cheers!
Hi Michael,
We have the exact config you posted above, but in reading about SMLT I’m confused about some details, and don’t really see how it’s better than PVSTP (other than perhaps a faster convergence). Some documents infer the IST is a routed link, others that it is a switched link. Some say no user traffic is sent across IST, but then how would you get redundant connectivity. Lastly, why would SLPP be needed if SMLT has already provided a loop-free redundant environment similar to PVSTP?
Thanks for any insight.
Neil
Hi Neil,
IST/SMLT/MLT are all Layer 2 technologies which can be coupled with Layer 3 protocols such as OSFP, VRRP, RSMLT to provide highly resilient networks.
The user traffic traversing the IST is minimized to a large degree but it can occur on occasion. In the event of a link failure to a closet then a large portion of traffic may need to traverse the IST to get back to resources (servers, etc) physically attached to that core switch.
You get redundant connectivity in that both links are active (not active/passive as with Spanning Tree). Traffic is split across both links using an algorithm that hashes the source and destination MAC addresses (this way the same conversation always flows over the same path). If a link fails all remaining traffic gets bridged/switched over the remaining SMLT link.
SLPP is a protocol design to detect edge switches that are not configured properly. The edge/closet switch needs to be configured with both uplinks in a MLT (Avaya) or Port Channel (Cisco). If the edge/closet switch isn’t configured as such it will loop the traffic between the two uplinks back to the core. SLPP is designed to detect that loop and shutdown only 1 on the uplinks thereby preserving connectivity to the closet while protecting the network from collapse.
Thanks for the comment!
Thank you for this post, it helps me a lot to validate my own configuration.
We are currently installing a new datacenter and needed to aggregate the link (black fiber) between our two sites. Our configuration is quite similiar to yours.
Thank you for the different “show commands” very helpful to validate our configuration (and discover that our ISP is a lazy boy).
Hi Michael,
We have 2 ers8600 smlt working but i can’t do mac based vlan trunking ,
-ers8600-a vlan1 port based vlan working on the other ers 8600-b but mac based vlan (vlan2) not working
Tahnk You,
Can you help me,
Hi Harry,
I haven’t see many implementations of MAC based VLANs, but I’m going to guess that both VLANs need to be configured the same on the ERS 8600 switches. So you should configure each VLAN the same way on the two ERS 8600 switches.
Cheers!
Hi Micheal,
i just have a problem, 2 ers 8600 working with smlt but, second ers8600 ip address renewing but very slow (First 8600 main system v3.x)
second 8600 on vlan
dhcp-relay enable
ip dhcp-relay create-fwd-path server 10.1.1.100
ip dhcp-relay enable-fwd-path server 10.1.1.100
I made these changes, but one thing has not changed
Hi Mikail,
This comment is kinda off-topic for this specific blog post.
Please post your problem in the discussion forums and I’ll be sure to reply.
Cheers!
Hi,
Can you explain to me how the avaya routing algorithm works when you have 2 x 4850 switches in a stack using SMLT connected to 2 x ERS8010 using 4 x 10gbps fibre connections. Why would a virtual machine route its traffic via one of the Core 8010 switches instead of the other?
The CPU on one of the 8080 switches was at 80% earlier and I could see that our scanning server was scanning all desktops using Core B and was wondering what determines that it chooses this route/core. Also, is it possible to spread the load over all uplinks, utilizing both core swicthes in order to spread the load?
Many Thanks,
John
Hi John,
This is covered in exhaustive detail elsewhere on the net… is’t a hash algorithm against the source and destination MAC addresses. The intent is that all the packets from a single conversation should flow over the same path, avoiding out of order frames, etc. That’s at Layer 2, if you when to Layer 3 (ECMP) you could do a round-robin as opposed to a hash. The load is caused by all the ARP packets trying to find all the desktops/laptops/servers/printers/etc in the network.
Cheers!