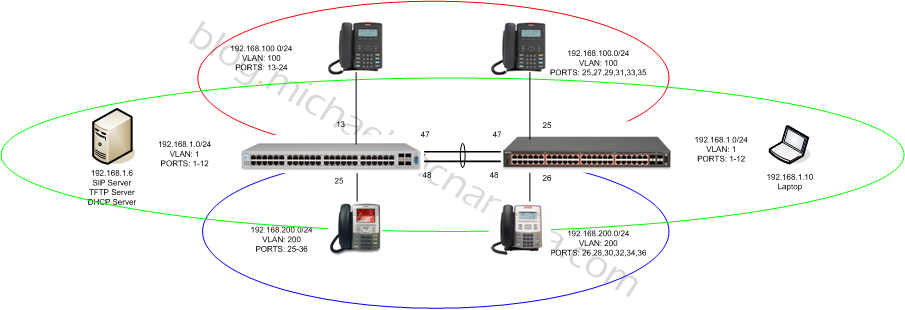
In my previous post I laid out the basics of how to configure multiple VLANs and enable IP routing on a stackable Avaya Ethernet Routing Switch. In this post I’m going to expand that topic to include trunking (802.1q) those VLANs to a second Ethernet Routing Switch. In this example I’ll add an Ethernet Routing Switch 4548 to the Ethernet Routing Switch 5520 that I had previously configured and deployed. We’ll create a Multi-Link Trunk between the two switches to bridge multiple VLANs across the 802.1q compliant link. Here’s a diagram of what the network should look like when we’re done;
In order to test I’ll move two of the IP phones to the Ethernet Routing Switch 4548 and I’ll use an old laptop to help verify the bridging.
Ethernet Routing Switch 4548
Let’s start with the Ethernet Routing Switch 4548GT-PWR and add the necessary configuration there first;
enable config t
We start by creating VLAN 100 and VLAN 200 on the Ethernet Routing Switch 4548;
vlan create 100 name "192-168-100-0/24" type port vlan members remove 1 25,27,29,31,33,35 vlan members add 100 25,27,29,31,33,35 vlan port 25,27,29,31,33,35 pvid 100 vlan create 200 name "192-168-200-0/24" type port vlan members remove 1 26,28,30,32,34,36 vlan members add 200 26,28,30,32,34,36 vlan port 26,28,30,32,34,36 pvid 200
I’m not going to create a Layer 3 IP interfaces on these VLANs since the Ethernet Routing Switch 5520 is already routing for us. We just want to bridge the frames between the two switches not route them (not in this post anyway). Now let’s configure the ports that will make up the Mulit-Link Trunk;
vlan port 47,48 tagging TagAll vlan members add 1 47,48 vlan members add 100 47,48 vlan members add 200 47,48 vlan port 47,48 pvid 1 mlt 1 disable mlt 1 name "MLT_to_ERS5520" mlt 1 learning disable mlt 1 member 47,48 mlt 1 enable
That’s pretty much it. We enabled tagging on the uplink/downlink ports, added the necessary VLANs to the ports and then created and enabled a MLT.
Ethernet Routing Switch 4548 – Show Configuration
That should be the configuration for the Ethernet Routing Switch 4548… let’s just have a quick look at the VLANs;
4548GT-PWR(config)#show vlan
Id Name Type Protocol User PID Active IVL/SVL Mgmt
--- -------------------- -------- ---------------- -------- ------ ------- ----
1 VLAN #1 Port None 0x0000 Yes IVL Yes
Port Members: 1-24,47-48
2 VLAN #2 Port None 0x0000 Yes IVL No
Port Members: 37-46
100 192-168-100-0/24 Port None 0x0000 Yes IVL No
Port Members: 25,27,29,31,33,35,47-48
200 192-168-200-0/24 Port None 0x0000 Yes IVL No
Port Members: 26,28,30,32,34,36,47-48
Total VLANs: 4
Let’s just check the Multi-Link Trunk configuration… if that’s wrong we could end up with a loop in the network;
4548GT-PWR(config)#show mlt 1 Id Name Members Bpdu Mode Status -- -------------------- ---------------------- ------ -------------- ------- 1 MLT_to_ERS5520 47-48 All Basic Enabled
You can see from the commands above that the ports are configured with the appropriate VLANs and the MLT is enabled.
Ethernet Routing Switch 5520
Let’s add the necessary configuration to the Ethernet Routing Switch 5520-PWR. I’m not going to repeat all the commands I performed in the yesterday’s post, instead I’ll just build upon the previous configuration adding what we need for the 802.1q trunking and the Multi-Link Trunking;
enable config t
vlan port 47,48 tagging TagAll vlan members add 1 47,48 vlan members add 100 47,48 vlan members add 200 47,48 vlan port 47,48 pvid 1 mlt 1 disable mlt 1 name "MLT_to_ERS4548" mlt 1 learning disable mlt 1 member 47,48 mlt 1 enable
Ethernet Routing Switch 5520 – Show Configuration
That should be the configuration for the Ethernet Routing Switch 5520… let’s just have a quick look at the VLANs;
5520-48T-PWR#show vlan
Id Name Type Protocol PID Active IVL/SVL Mgmt
--- -------------------- -------- ---------------- -------- ------ ------- ----
1 test Port None 0x0000 Yes IVL Yes
Port Members: 1-12,37-48
100 192-168-100-0/24 Port None 0x0000 Yes IVL No
Port Members: 13-24,47-48
101 10-101-20-0/24 Port None 0x0000 Yes IVL No
Port Members: 25-36
200 192-168-200-0/24 Port None 0x0000 Yes IVL No
Port Members: 47-48
Total VLANs: 4
Let’s just check the Multi-Link Trunk configuration… if that’s wrong we could end up with a loop in the network;
5520-48T-PWR#show mlt 1 Id Name Members Bpdu Mode Status Type -- ---------------- ---------------------- ------ -------------- ------- ------ 1 MLT_to_ERS4548 47-48 All Basic Enabled Trunk
Since all stackable Avaya Ethernet Routing Switches support Auto-MDIX I can just use two regular CAT5e patch cables to connect the switches together. If the switches didn’t support Auto-MDIX I would need to use two crossover cables between them.
Ethernet Routing Switch 4548 – Operational Status
With link up on ports 47 and 48 I can check the following information. The topology table will show me the physical connections between the two switches. The MAC/FDB table will show me that there are multiple MAC/FDB entries in VLANs 100 and 200 being learned across “Trunk 1”. The LLDP table will show me the Avaya IP phones that I’ve connected to ports 25 and 26.
4548GT-PWR#show autotopology nmm-table
LSlot RSlot
LPort IP Addr Seg ID MAC Addr Chassis Type BT LS CS RPort
----- --------------- -------- ------------ ---------------- -- --- ---- -----
0/ 0 192.168.1.25 0x000000 001E7E7C2C01 4548GT-PWR 12 Yes HTBT NA
1/47 192.168.1.50 0x000130 001F0ACEBC01 5520-48T-PWR 12 Yes HTBT 1/48
1/48 192.168.1.50 0x00012f 001F0ACEBC01 5520-48T-PWR 12 Yes HTBT 1/47
4548GT-PWR#show mac-address-table
Mac Address Table Aging Time: 300
Number of addresses: 20
MAC Address Vid Source MAC Address Vid Source
----------------- ---- ------- ----------------- ---- -------
00-02-B3-CB-77-A2 1 Port:19 00-04-61-9E-46-7E 1 Port:21
00-0C-29-64-33-F9 1 Port:19 00-0C-29-A5-CB-54 1 Port:19
00-18-01-EA-F4-45 1 Port: 1 00-1C-11-6B-DC-6B 1 Port: 1
00-1C-11-6D-15-27 1 Port: 1 00-1C-11-6D-15-DC 1 Port: 1
00-1E-7E-7C-2C-00 1 00-1E-7E-7C-2C-40 1
00-1F-0A-CE-BC-40 1 Trunk:1 00-1F-D0-D0-BE-2D 1 Port:17
00-23-EE-96-AA-21 1 Port: 1 00-24-B5-F6-94-02 1 Trunk:1
00-0A-E4-76-9C-C8 2 Port:45 00-1F-0A-CE-BC-01 2 Trunk:1
00-24-DC-DF-0D-08 2 Port:43 00-A0-F8-5E-CE-BC 2 Port:39
00-1F-0A-CE-BC-41 100 Trunk:1 00-24-7F-99-84-70 100 Port:25
00-24-7F-99-84-E9 100 Trunk:1 00-1E-CA-F3-1D-B4 200 Port:26
4548GT-PWR#show lldp neighbor
-------------------------------------------------------------------------------
lldp neighbor
-------------------------------------------------------------------------------
Port: 26 Index: 4 Time: 13 days, 22:42:31
ChassisId: Network address IPv4 192.168.200.5
PortId: MAC address 00:1e:ca:f3:1d:b4
SysCap: TB / TB (Supported/Enabled)
PortDesc: Avaya IP Phone
SysDescr: Avaya IP Telephone 1120E, Firmware:SIP1120e04.00.04.00
-------------------------------------------------------------------------------
Port: 25 Index: 6 Time: 13 days, 22:43:48
ChassisId: Network address IPv4 192.168.100.98
PortId: MAC address 00:24:7f:99:84:70
SysCap: TB / TB (Supported/Enabled)
PortDesc: Avaya IP Phone
SysDescr: Avaya IP Telephone 1220, Firmware:SIP12x004.00.04.00
-------------------------------------------------------------------------------
Sys capability: O-Other; R-Repeater; B-Bridge; W-WLAN accesspoint; r-Router;
T-Telephone; D-DOCSIS cable device; S-Station only.
Total neighbors: 2
Ethernet Routing Switch 5520 – Operational Status
I can check all the same information on the ERS5520.. The topology table will show me the physical connections between the two switches. The MAC/FDB table will show me that there are multiple MAC/FDB entries in VLANs 100 and 200 being learned across “Trunk 1”. The LLDP table will show me the Avaya IP phones that I’ve connected to ports 13 and 25.
5520-48T-PWR#show autotopology nmm-table
LSlot RSlot
LPort IP Addr Seg ID MAC Addr Chassis Type BT LS CS RPort
----- --------------- -------- ------------ ---------------- -- --- ---- -----
0/ 0 192.168.1.50 0x000000 001F0ACEBC01 5520-48T-PWR 12 Yes TPCH NA
1/47 192.168.1.25 0x00012f 001E7E7C2C01 4548GT-PWR 12 Yes TPCH 1/47
1/48 192.168.1.25 0x000130 001E7E7C2C01 4548GT-PWR 12 Yes TPCH 1/48
5520-48T-PWR#show mac-address-table
Mac Address Table Aging Time: 300
Number of addresses: 16
MAC Address Vid Source MAC Address Vid Source
----------------- ---- ------- ----------------- ---- -------
00-02-B3-CB-77-A2 1 Trunk:1 00-04-61-9E-46-7E 1 Trunk:1
00-0C-29-64-33-F9 1 Trunk:1 00-0C-29-A5-CB-54 1 Trunk:1
00-18-01-EA-F4-45 1 Trunk:1 00-1C-11-6B-DC-6B 1 Trunk:1
00-1C-11-6D-15-27 1 Trunk:1 00-1C-11-6D-15-DC 1 Trunk:1
00-1E-7E-7C-2C-01 1 Trunk:1 00-1E-7E-7C-2C-40 1 Trunk:1
00-1F-0A-CE-BC-00 1 00-1F-0A-CE-BC-40 1
00-1F-D0-D0-BE-2D 1 Trunk:1 00-23-EE-96-AA-21 1 Trunk:1
00-24-B5-F6-94-02 1 Port: 9 00-1F-0A-CE-BC-41 100
00-24-7F-99-84-70 100 Trunk:1 00-24-7F-99-84-E9 100 Port:15
00-1E-CA-F3-1D-B4 200 Trunk:1
5520-48T-PWR#show lldp neighbor
-------------------------------------------------------------------------------
lldp neighbor
-------------------------------------------------------------------------------
Port: 13 Index: 5 Time: 0 days, 00:02:00
ChassisId: Network address IPv4 192.168.100.4
PortId: MAC address 00:24:b5:f6:94:02
SysCap: TB / TB (Supported/Enabled)
PortDesc: Avaya IP Phone
SysDescr: Avaya IP Telephone 1165E, Firmware:SIP1165e04.00.04.00
-------------------------------------------------------------------------------
Port: 25 Index: 6 Time: 0 days, 00:02:19
ChassisId: Network address IPv4 192.168.200.99
PortId: MAC address 00:24:7f:99:84:e9
SysCap: TB / TB (Supported/Enabled)
PortDesc: Avaya IP Phone
SysDescr: Avaya IP Telephone 1220, Firmware:SIP12x004.00.04.00
-------------------------------------------------------------------------------
Sys capability: O-Other; R-Repeater; B-Bridge; W-WLAN accesspoint; r-Router;
T-Telephone; D-DOCSIS cable device; S-Station only.
Total neighbors: 2
Would you be interested in seeing a screencast of this whole process?
Let me know if you have any questions or would like to point out corrections!
Cheers!
How can I create a trunk between two ERS 4500 devices if there is only one port used for the trunk? The specific device is ERS 4526t-pwr, and they are connected via fiber in port 25. We are using a fiber transceiver. I am unable to create the trunk using one port.
Hi Khalil,
You can following the steps outlined in the post above, just skip the parts referring to the MultiLink Trunk (MLT) since you only have a single port.
Good Luck!
Thanks Michael. Do the VLAN’s need to match across the switches? Must VLAN 100 be defined the same way on both switch 1 and 2? Or can VLAN 100 on switch 1 correspond to VLAN 200 on switch 2 and vice versa?
The VLAN IDs need to match across your switches (network).
Cheers!
What if my two vlan’s do not span the switches? Each vlan is only on one switch, but the two vlan’s need to talk to each other and they are connected via fiber on port 25 on each switch. Would the following commands work for me:
First SWITCH (192.168.1.0)
=============
enable
configure terminal
vlan name 1 “First”
vlan port 1-24 pvid 1
interface vlan 1
ip address 192.168.1.251 255.255.255.0 1
exit
vlan create 100 name “Second” type port
vlan members add 100 25
interface vlan 100
ip address 10.1.10.253 255.255.255.0 2
exit
ip routing
Second SWITCH (10.1.10.0)
=========
enable
configure terminal
vlan name 1 “Second”
vlan port 1-24 pvid 1
interface vlan 1
ip address 10.1.10.251 255.255.255.0 1
exit
vlan create 100 name “First” type port
vlan members add 100 25
interface vlan 100
ip address 192.168.1.253 255.255.255.0 2
exit
ip routing
Your confusing switching/bridging with routing. Looking at your configuration it appears that you want to route between VLANs.
You should create a management VLAN which you can also use as your backbone transport. You should avoid using VLAN 1 as a best practice, it can save you issues down the road. This VLAN should be extended (bridged) to all your switches, we’ll use it to connect your different VLANs at Layer 3 and route across the VLANs.
You should also clean up your VLAN assignments… you’ve got 10.1.10.x on VLAN 1 on the 2nd switch but on the 1st switch it’s VLAN 100.
You need to clean that up first… VLAN 10 = 10.1.10.0/24 and VLAN 20 = 192.168.1.0/24. Your VLANs need to be unique and match across your entire network.
You’ll find a lot of good reading over on the discussion forums; http://forums.networkinfrastructure.info/nortel-ethernet-switching/
Once you’ve completed your clean up here’s how you would go about enabling routing.
ERS-4548 A (First Switch)
You should start by making sure your fiber uplink/downlink is set for tagging (trunk).
vlan port 24 tagging TagAll
Now let’s create the management VLAN and assign an IP address (172.16.10.1);
vlan create 200 name “Management” type port
vlan members add 200 24
interface vlan 200
ip address 172.16.10.1 255.255.255.0 3
exit
ip routing
Now we need to create some routes to tell this switch (ERS-4548 A) to send traffic for 10.1.10.0/24 to ERS-4548 B;
ip route 10.1.10.0 255.255.255.0 172.16.10.2 1
ERS-4548 B (Second Switch)
You should start by making sure your fiber uplink/downlink is set for tagging (trunk).
vlan port 24 tagging TagAll
Now let’s create the management VLAN and assign an IP address (172.16.10.2);
vlan create 200 name “Management” type port
vlan members add 200 24
interface vlan 200
ip address 172.16.10.2 255.255.255.0 3
exit
ip routing
Now we need to create some routes to tell this switch (ERS-4548 B) to send traffic for 192.168.1.0/24 to ERS-4548 A;
ip route 192.168.1.0 255.255.255.0 172.16.10.1 1
Good Luck!
Wow, this is great! Thank you so much!
Just a few notes:
-The fiber uplink/downlink is on port 25.
-I will only create the first vlan on the first switch and the second vlan only on the second switch. Must the first vlan be created on the second switch and the second vlan on the first switch?
I am going to reset both switches and here are the commands I will run:
ERS-4526 (First Switch)
enable
configure terminal
vlan name 10 “First”
vlan port 1-24 pvid 10
interface vlan 10
ip address 192.168.1.251 255.255.255.0 1
exit
vlan port 25 tagging TagAll
vlan create 200 name “Management” type port
vlan members add 200 25
interface vlan 200
ip address 172.16.10.1 255.255.255.0 3
exit
ip routing
ip route 10.1.10.0 255.255.255.0 172.16.10.2 1
ERS-4526 (Second Switch)
enable
configure terminal
vlan name 20 “Second”
vlan port 1-24 pvid 20
interface vlan 1
ip address 10.1.10.251 255.255.255.0 1
exit
vlan port 25 tagging TagAll
vlan create 200 name “Management” type port
vlan members add 200 25
interface vlan 200
ip address 172.16.10.2 255.255.255.0 3
exit
ip routing
ip route 192.168.1.0 255.255.255.0 172.16.10.1 1
Still no luck wiht this. After putting in the commands below I am NOT able to ping from one switch to the other. Could you review my commands to point out what I could be doing wrong?
ERS-4526 (First Switch)
enable
configure terminal
vlan configcontrol flexible
vlan create 10 name “First” type port
vlan members add 10 1-24
vlan port 1-24 pvid 10
interface vlan 10
ip address 192.168.1.251 255.255.255.0 2
exit
vlan port 25 tagging TagAll
vlan create 200 name “Management” type port
vlan members add 200 25
interface vlan 200
ip address 172.16.10.1 255.255.255.0 3
exit
ip routing
ip route 10.1.10.0 255.255.255.0 172.16.10.2 1
ERS-4526 (Second Switch)
enable
configure terminal
vlan configcontrol flexible
vlan create 20 name “Second” type port
vlan members add 20 1-24
vlan port 1-24 pvid 20
interface vlan 20
ip address 10.1.10.251 255.255.255.0 2
exit
vlan port 25 tagging TagAll
vlan create 200 name “Management” type port
vlan members add 200 25
interface vlan 200
ip address 172.16.10.2 255.255.255.0 3
exit
ip routing
ip route 192.168.1.0 255.255.255.0 172.16.10.1 1
What IP address did you try to ping? I would start with trying to ping the 176.16.10.x IP address. Since both switches on connected to that VLAN (network) there’s no routing really required. If you can’t ping then you need to check your configuration and verify that VLAN 200 is being bridged properly and that your IP interface on VLAN 200 is configured properly.
Cheers!
I can ping the interfaces successfully. From switch 1 I am able to ping the following:
192.168.1.251 (VLAN 1 Interface of Switch 1)
172.16.10.1 (VLAN 200 Interface of Switch 1)
10.1.10.251 (VLAN 1 Interface of Switch 2)
172.16.10.2 (VLAN 200 Interface of Switch 2)
But if I try to ping an IP which is on the second switch from the first switch, that fails. For example, if I try to ping 10.1.10.1 from the first switch that fails. But I can reach the two interfaces on the second switch.
Do you know what I could be missing?
What is 10.1.10.1?
10.1.10.1 is a computer connected to the second switch.
I was able to get everything working. The issue was I needed to change the default gateway on the clients. The default gateway was still pointing to the server that did routing before.
But I still have one problem: On each switch there is a DHCP server and I am unable to stop the DHCP server on one switch servicing clients on the other switch. Each DHCP server should be limited ot their own switch or vlan.
I’m glad to hear you were able to figure it out.
If you have additional questions please post them over on the discussion forums.
Cheers!
Hi Michael,
Is it necessary to this: ??
what is the point to add them to all the vlan??
Thanks in advance.
Hi Chew,
The commands above are adding the VLANS 1,100,200 to the uplink ports of 47 and 48. If you don’t add the VLANS to the uplink port the clients in those VLANs won’t be able to communicate with the other devices in the network. You will obviously use different VLAN numbers than I’ve provided in this example.
Good Luck!
Hi Michael,
Thanks for your reply. I still have little confusion on it as previously I am using CISCO.
As I saw there is a command vlan port 47,48 tagging TagAll , is it means that these both port will untag all the tag frame and send it over across the other swicth??
As previously in cisco switch, it seems like it doesn’t need to add the trunk link port to other vlan. Am I correct?
Can you explain more?? especially the AVAYA.
Thanks a lot in advance.
Hi Chew,
The command vlan port 47,48 tagging TagAll will make these two ports 802.1q trunk ports. All frames will be tagged with an 802.1q header including the appropriate VLAN ID.
With Cisco switches a trunk port automatically includes all VLANs defined on the switch. With Avaya switches you need to manually configure which VLANs you’d like trunked across those ports.
You can read more about it here;
http://blog.michaelfmcnamara.com/2012/02/untagall-vs-tagall-on-avaya-ethernet-routing-switches/
Good Luck!
HI Michael,
I see. Now I get it. Thanks a lot ya!!
Hi Michael,
Please reply me. I seriously need help.
Thanks a lot!
Hi Michael, nice blog
I have two Avaya 3526T switches with the following configuration:
Switch 1 ip routing enable
USERS vlan 10
192.168.12.2 255.255.255.192
PHONES vlan 64
192.168.12.65 255.255.255.192
MANAGEMENT vlan 240
ip address switch 192.168.12.245 255.255.255.248 default-gateway 192.168.12.1
port 25 pvid 240 tagall
Switch 2
USERS vlan 10
PHONES vlan 64
MANAGEMENT vlan 240
ip address switch 192.168.12.246 255.255.255.248 default-gateway 192.168.12.1
port 25 pvid 240 tagall
Switch 2 as you said uses switch 1 for routing, my router is member of USERS vlan. I would like to manage my two switches from a users PC but only switch 1 is reachable to ping, I´m not able to ping switch 2, Am I doing something wrong?
Hi Jhon,
You’d need to verify that you have set the management VLAN on switch 2 (vlan mgmt 240). You’d also need to verify that you are extending VLAN 240 to whatever switch/router is going to act as the gateway for that VLAN. And lastly you’d also need to verify that you have the proper static/dynamic routes in place for routing to function to/from 192.168.12.246.
Good Luck!
OK I followed your preciding instructions, I have set management vlan 240 on both switches SW1 192.168.12.245 and SW2 192.168.12.246, just SW1 routing enable. Everything works fine however:
1) I just can see SW1 from a users PC but now I´m confused with a post by you that I read in forums.networkinfrastructure “You really don’t need a dedicated management VLAN once the switch starts acting as a Layer 3 switch as opposed to a Layer 2 switch” what does it mean? and I can´t set a CLIP as you said.
2) The only way I can see both switches from users vlan is enabling ip routing and creating vlans on both switches with same IP address to match across the switches everything works fine but when I do that I can see this error message in console “arp operation failed, errno: Invalid argument” I believe that it happens because I have the same vlan on both switches with same name, same ID, same IP address but with different MAC address.And finally.
3) If my switches are working as layer 3, do I need a default gateway?
4) I´m going crazy hahaha!
Thanks for your help in advance.
Hi Jhon,
1) What model of switch? Not every model support CLIP or Loopback interfaces, for those switches it’s either an IP interface associated with a VLAN or the management IP address.
2) You can either route or bridge between your switches (actually you can do both but lets ignore that fact right now). If you bridge using an 802.1q trunk then you should be able to communicate so long as you have the proper route table entries.
3) Yes.
4) No, your learning.
Cheers!
thanks for your help Michael
1) ERS 3526T-PWR
2) Actually, I´m confused between bridge and routing, but now I have a new problem, one of my switches is in a branch office and I want to have remote management from my central office however I need to have access through management ip address 192.168.53.245 because of we have to follow a standard
————————————————-
!Users Vlan 62 ! Mgmt Vlan 240 !
————————————————-
! !
ROUTER Management IP
192.168.53.1/192 192.168.53.245/248
But When I send a ping to switch in vlan 240 I don´t have a reply, I just can ping to switch in users vlan 192.168.53.62, checking Avaya routing manage i found that I need a management route to do what I want, but in manual I can see that router is member of management vlan and I have my router in users vlan. is there a way to solve my problem without change my router to management vlan?
Bye
You need a default route for the switch to respond to any packets outside of the management VLAN. While you might have a route to the switch in your desktop/laptop the switch doesn’t know where to send the reply packets for the 192.168.53.0/192 network.
Look at the routes in my lab switch;
4548GT-PWR>show ip route =============================================================================== Ip Route =============================================================================== DST MASK NEXT COST VLAN PORT PROT TYPE PRF ------------------------------------------------------------------------------- 0.0.0.0 0.0.0.0 192.168.1.1 1 1 1 S IB 5 192.168.1.0 255.255.255.0 192.168.1.25 1 1 ---- C DB 0 Total Routes: 2 ------------------------------------------------------------------------------- TYPE Legend: I=Indirect Route, D=Direct Route, A=Alternative Route, B=Best Route, E=Ecmp Route, U=Unresolved Route, N=Not in HWThe management VLAN by default is VLAN 1, in this case I’ve configured the switch IP address as 192.168.1.0. I’ve also added a default route to 192.168.1.1 which is the primary router in my lab.
If you only have this single ERS 3500 series switch then you must enable Layer 3 (routing) in order to be able to ping the management VLAN. That’s the difference between a Layer 2 switch and Layer 3 switch. With a Layer 2 switch you need a router to connect the different networks and subnets.
Good Luck!
Hello Michael
I have a switch 4548GT-PWR, I need comunicate two vlans, I saw your blog but I did the same that your examples and I can not comunicate the vlans this is my configuration, Can you help me please.
vlan create 10 name ITCJ type port
vlan members remove 1 1-5
vlan members add 10 1-5
vlan port 1-5 pvid 10
vlan create 20 name CTTI type port
vlan members remove 1 5-8
vlan members add 20 5-8
vlan port 1-5 pvid 20
interface vlan 10
ip address 192.168.10.1 255.255.255.0 1
interface vlan 20
ip address 192.168.20.1 255.255.255.0 2
so how can I comunicate these vlans, i do not have a router
Hi David,
What version of software in on the RES 4548GT-PWR? If you have software release 5.4 or later you should have the command “ip routing” which will enable the Layer 3 routing functionality in the switch. Assuming this is the only router in your environment you just need to set the devices in VLAN 10 and 20 with their respective default gateways of 192.168.10.1 and 192.168.20.1 and you should be good to go.
You’d probably benefit from reading this blog post, http://blog.michaelfmcnamara.com/2011/01/vlans-ip-routing-ethernet-routing-switch/
Good Luck!
Michael,
Your posts are very informative. I find myself in the unique situation of having to take over a Network of Nortel switches, having not used Nortel before. My core switches in the configuration are HP, and there are Nortel and HP switches co-mingled througout the network. We already deployed our new network configuration across my core HP switches. We are going to take over the Nortel switches. I do not think I need to start from scratch (factory default) on the Nortels. I think it should be as easy as adding my VLANs to the Nortel switches (I am lucky I picked VLAN numbers that did not already exist in Nortel) and then tagging/untagging ports. I know all VLANs need to be added to the fiber ports for network communication (and I can use your commands above for that). I need help with the following commands if you don’t mind?
VLAN 1 is my management VLAN, and the only thing that needs an IP address, but I do need to change/remove the gateway. My switches are on the same IP scheme as the Nortels, but the gateway will cause issues.
1) Remove the password from a Nortel switch
2) Remove the gateway from VLAN 1
2) remove existing tag/untag from ports
3) in the above posts, I see no mention of “untag”. We use “untag” a lot in HP switches. How do I “untag” ports in Nortel?
My other “thought” is that I could use the existing VLAN’s on the Nortel switches and run a patch cable from my VLAN on my switch, to one of the ports on the existing Nortel VLAN and bridge the communication that way without changing VLANS. I am not sure if I am off base or not.
Hi Jon,
It’s not hard to understand Avaya (formerly Nortel) switches they behave by the same principles but have slightly different terminology.
unTagAll – access port with a single VLAN associated
TagAll – trunk port with all VLANs getting 802.1q tag headers
unTagPVIDonly – trunk port with the PVID VLAN untagged all other VLANs getting 802.1q tag headers
In an unTagAll configuration the PVID of the port should be set the only VLAN assigned to the port. In a TagAll configuration the PVID is best set to the management VLAN of the network.
It’s highly advisable to NOT use VLAN 1 (the default VLAN on all factory reset switches) as a best practice if at all possible.
If you have additional questions this post might help, http://blog.michaelfmcnamara.com/2012/02/untagall-vs-tagall-on-avaya-ethernet-routing-switches/
Good Luck!
I am only using VLAN 1 for management of the switches, nothing else. I think I will be ok there.
I apologize as I dont know what PVID means in this context, its not required in HP networking. This is for a hotel wireless/wired guest room network.
VLAN 1 = switch management
VLAN 61 = public IP addresses (facing outside)
VLAN 71 = wireless AP management network
VLAN 91 = guest facing network.
On my HP switches, uplink/fiber ports between switches obviously have all VLAN’s tagged. In the HP switches, a wired guest room port would be “VLAN 91 untag”. A wireless AP would be “VLAN 71 untag” and “VLAN 91 tagged”
Can you help me accomplish this with minimal pain? HAHA. Most of the Nortel switches will only have wired guestroom network ports, so besides the uplinks I don’t have a lot of VLAN modifications to do.
Hi Joe,
The PVID is the default VLAN for that port. With access ports as in UnTagAll ports the PVID should be set to the same VLAN ID as the VLAN assigned to that port. For example, if port 10 was a member of VLAN 200 the PVID for port 10 would be 200. In the case of a trunk port (802.1q) with UnTagPVIDOnly the PVID is the VLAN that will be sent untagged across the link. In the case of a traditional trunk port (802.1q) the PVID should usually be set to the management VLAN, with discard-untagged-frames enable to prevent any accidental configuration issues.
If you wanted ports 10-15 in VLAN 61 you would issue the following commands;
You do need to check and make sure that Spanning Tree is enabled after making any VLAN changes
You can refer to this blog post for a best practice configuration of an ERS 5520 switch.
http://blog.michaelfmcnamara.com/2007/10/nortel-ers-5520-pwr-switch/
Good Luck!
Hi Micheal,
This is a nice post you have here but I have a question. I made vlans on a nortel 3510-24t switch just like in your previous post. they are working, I have a cisco switch 3550 that I want to configure some of the vlans like on the nortel switch. How can i create a trank between the cisco and the nortel switch? so that their will not be any communication problem between them?
Thanks.
Hi McAdams,
You probably want to look at this post entitled, 802.1Q VLAN Tagging on a Cisco Catalyst 3750-E.
Good Luck!
Hi Micheal, I forgot, on the vlans! how can i control bandwidth so that vlan A will have higher bandwidth than vlan B on a nortel switch 3510-24t? and how can i make Vlan A not to communicate with vlan B, but vlan A to communicate with vlan C ?
While it’s technically possible using the QoS filters it’s really not practical.
Hello,
I hope that somebody (Michael! pls help!) may help me.
I have a running tack with 3 units (5500) with some VLANs working correctly. Routing between then work perfectly, also the routing to the default ruting (throw a aditional VLAN).
Problem comes when I set a pair of new VLANs. It is done correctly but I cant ping the ip address assigned to the VLAN either to route anything.
I have noticed that no new LOCAL route appear when I set the IP address of the new VLANS so, whats is happening? why is not any route appearing when I set the IP address of VLANS?
global ip routing is active, and there are VLANs working… Do you have a clue of what should be the problem?
I have follow the step than you have defined to create the new VLANs , IPs and dhcp relay, also I did it using the web interface. After 5 tries I am a bit lost.
Could you help me please?
Alberto.
You will not see any route in the routing table until that VLAN is active. In order for the VLAN to be active you need to have at least 1 port that is a member of that VLAN up (link) and running. Now with that said there is a bug in some specific versions of software where the VLAN will not become active, you can test this case by just rebooting the switch and see if that clears the problem. If so then upgrade to the latest software release to resolve the problem.
Cheers!
Hi Micheal,
If I want to put a trunk from a nortel to a non nortel switch with only vlan 100 passing the trunk is this config correct?
________________________________________
vlan port 10-12 tagging tagall
vlan members add 1 10-12
vlan members add 100 10-12
vlan 10-12 pvid 1
_______________________________________
in the last line:
why would i need pvid 1 instead of pvid 100, in which vlan 100 is the only vlan that i want from the other switch?
Hi Michael,
i wanna create 3 vlan, 2 vlan data and 1 vlan voice.
in my Office a Switch connected to IP telephones before connect to PC.
how to untagged 2 vlans (voice and data) in one port? please give me some syntax/command for Nortel switch. I have done it in cisco and procurve, but i dont similiar with nortel switch.
help me please.
Thanks
Here again just to say thank you, you save my life with your blog.
Great blog!
What’s the difference between basic and advanced “Loadbalance(Mode)”?
Thanks!
-b
Hi Michael, am new to avaya just got 1 from my coy to practice on, though have try configurations in packet tracer by cisco for creating vlan i.e # enable …… config t , vlan 100 0r 20 as required, but i tried to do same procedure like cisco swithes but i was hook as the avaya doesent recognized those command instead it require some command like i.e vlan create something like that, my question now is isn’t and all those command stuffs should be same ? pls help
Hi Muhammad,
Unfortunately the commands are not the same across manufacturers. That’s not to say that a great many manufacturers are trying to emulate the Cisco CLI these days. While the commands are similar for the majority of vendors they are not identical. I’m sure for a time the other manufacturers worried about Cisco taking them to court similar to how Apple took Microsoft to court over Windows 3.1.
Good Luck!
Michael, I need to configure 802.1q tunneling where 4 VLANs of a client reach another branch of that client througt my cloud MSTP. The switch models are ERS4800. Is there any way to do this with avaya switches?
Thanks!
If the provider supports Q-in-Q you could just tag 802.1Q taffic across your providers network. If they don’t support Q-in-Q you would need to either route (Layer 3) or you could do some type of GRE tunnel with a Cisco or Juniper router.
Cheers!
Hello sir,
I read your blog but my question is
If I will connect another Ethernet routing switch then how I will configure means two l3 switch
Hi Deepak,
You shouldn’t configure both for L3… you need to configure L2 between the 2 switches so they can share VLANs (unless you are going to stack them) and then only one of them will act as the L3 between VLANs.
Now there are switches you can use from Cicso (vPC) and Extreme (formerly Avaya) (IST) and others that allow you to run 2 switches under a single dataplane but that’s for enterprise HA and redundancy in conjunction with protocols such as HSRP and VRRP.
Cheers!